
On November 28, 2017, a bug was disclosed in macOS High Sierra that lets an attacker bypass administrator authentication without supplying the administrator's password.
Apple has released a security update to patch this vulnerability. If you are running macOS High Sierra 10.13 or higher, please update your Mac to High Sierra 10.13.1 as soon as possible and then install Security Update 2017-001.
What is the issue?
A security vulnerability in macOS High Sierra was discovered that allows anyone to log into a Mac running High Sierra by exploiting the "root" user. By taking advantage of this vulnerability, anyone could access the administrator's account without providing the password.
How is Apple responding to this vulnerability?
Apple became aware of this issue soon after it was discovered, and they have released a security update to correct it. Security Update 2017-001 provides improved credential validation and ensures that your Mac is safe from this bug.
Are all Macs affected?
No. The only Macs affected are those running macOS High Sierra 10.13 or higher. If you are running macOS Sierra 10.12.6 or earlier, you are not affected.
How do I check what software my Mac is running?
Click the apple icon in the top-right corner of your screen and select About This Mac. A box will appear on your screen. Your computer's software version is displayed under the Overview tab.

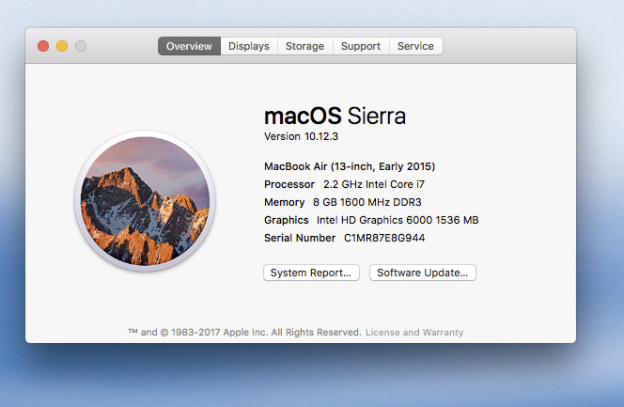
What are my next steps?
If you are operating on macOS High Sierra 10.13, update your system to version 10.13.1 as soon as possible, then install Security Update 2017-001.
To check for and download software updates:
-
Open the App Store on your Mac.
-
In the App Store toolbar, click Updates.
-
Any available updates will be listed. Click the Update button to the right of each update to download and install.
Learn more from the Apple Support Guidelines.
How is the university responding to this vulnerability?
Information Services and Technology (IST) recommends that users update their Macs as soon as possible. Additionally, the high-risk network port Virtual Network Computing (VNC) is now blocked at the university's internet gateway. VNC can be used to remotely execute this Apple macOS High Sierra exploit. It is extremely insecure, derived from legacy technology, and is currently unnecessary as there are much more preferable and secure means.
If you currently use VNC to remotely connect to your university resources, you need to connect to the university's Virtual Private Network (VPN) service first. The VPN service protects both you and the university with respect to remote connectivity.
More information on the VPN service is available at https://ist.ualberta.ca/services/networking/vpn
If you have any questions or issues, please contact the Staff Service Centre (updated 2024).